ExamNotes for Network+ N10-007 1.1 Explain the purposes and uses of ports and protocols – Part 1 of 2
Welcome to exam notes for Network+ N10-007!
Click here to go back to the Network+ ExamNotes Table of Content
ExamNotes is one article for each and every one of the CompTIA Network+ sub-objectives. This one addresses sub-objective 1.1 “Explain the purposes and uses of ports and protocols”.
Click here if you want to view a video walkthrough of a Performance Based Question
Because this sub-objective covers so much ground we have split it up into two parts and this is part 1 of 2. Click here for Part 2.
We need your help! This is a free community resource: Please give us any feedback you deem appropriate. If you like it as is, we’d love to know. If you don’t like it, we’d love to know how to improve it – your fellow students will all benefit from your feedback.
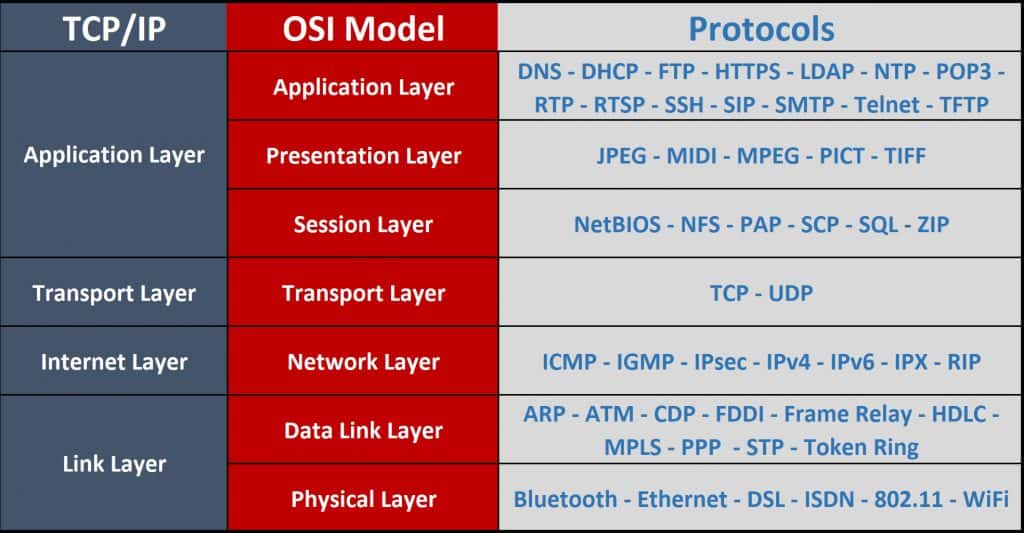
Protocols and Ports
A protocol is basically the agreement between devices defining how these networked devices will exchange data. Protocols are often used together to take advantage of the particular protocols strengths as you will see below. TCP/IP is a prime example of this type of combination, where IP is responsible for transmitting data without establishing a session. This means the packets can take any possible route to the correct host, resulting in messages that arrive out of sequence. TCP then ensures the transmission is reliable. The Network+ exam objectives list the Protocol and the Port it uses together. The Port number is used to deliver the data of a specific process. For example, a transmission using HTTP protocol will be delivered to Port 80 by default.
– SSH 22
The Secure Shell (SSH) protocol opens a secure network channel that provides confidentiality and integrity for network services over an unsecured network using public key cryptography. This makes it a cryptographic network protocol. It is used to secure remote network logins and other confidential data. Passwords cannot be intercepted because the encryption is established before the login is required.
– DNS 53
The Domain Name System (DNS) is mostly known for its function of translating friendly domain name URLs like www.mysite.com into its actual IP address. These a human is less likely to remember (think IPv6!).
DNS uses two protocols: TCP and UDP on port 53. DNS servers update themselves using and maintaining a list of known host to address translations in a distributed database while obtaining unknown or moved domains. This supports the hierarchical nature of domain naming of domains and sub-domains. Each domain will have a designated authoritative name server to manage the domains and sub-domains and to communicate that information to the database.
– SMTP 25
The Simple Mail Transport Protocol (SMTP) uses TCP port 25 for internet mail transmission. It is an internet standard protocol. Due to the proliferation of SPAM and other email related vulnerabilities, other ports can be used, most notably port 587. A secure nonstandard implementation of this protocol is SMTPS which is not standard but quite effective because it is one of the protocols that can utilize SSL. SMTP is responsible for the transmission of email between servers and for sending email from a client. Other protocols are used for the reception of email on the client.
– SFTP 22
The Secure File Transfer Protocol (SFTP) is a secure and encrypted protocol that is based on the SSH protocol. It is the secure alternative to FTP.
– FTP 20, 21
The File Transfer Protocol is used in a client/server configuration to transfer files. It can operate in active or passive mode and uses TCP to control the connection. In active mode, the connection is initiated by the client. It informs the server about which port it intends to use to receive data. In active mode (although port 21 is used for command and control), the data will be sent out on port 20 which serves as the FTP servers data port. Passive mode is used in situations where inbound client TCP connections are not possible. Firewalls generally block inbound connections by default. Here the client sends a PASV command to the server and the server determines which client port can be used for the transfer.
– TFTP 69
The Trivial File Transfer Protocol (TFTP) is a simplified version of FTP. It does not offer features like authentication and remote directory viewing. It is light, fast but insecure.
– TELNET 23
Developed in the late 60’s, Telnet was designed to support remote logins and communication between computers in what was a “kinder and gentler” time for networks. It provides a functional command prompt on the remote host. These are plaintext and communication channels making them subject to interception. Today’s networks and the internet are not a place where this is acceptable and so Telnet is now considered obsolete. Telnet does not encrypt data, SSH has generally replaced Telnet for these connections.
– DHCP 67, 68
The Dynamic Host Configuration Protocol (DHCP) has saved years of man hours and countless misconfigurations. As the most common IPv4 or IPv6 TCP/IP addressing method DHCP is responsible for the complete client configuration on a TCP/IP network. On a work network, there is usually an assigned DHCP server. Residential or SOHO implementations use the router provided by the ISP to perform this function. What DHCP does is assign or lease a unique IP address to each host. The duration of the lease is determined by the network administrator or weekly by default. It will define the internet gateway and Domain Name Server to be used. This means that your machine may not get the same IP address when rebooted or otherwise disconnected. The DNS and Gateway settings will remain. The DHCP server has an available pool of IP addresses available to assign to clients (hosts) that attempt to connect to the network. The client broadcasts a UDP discovery packet for an address to all connected networks. All DHCP servers will offer an address to the client then the client will accept the offer from the nearest server by requesting a lease and that server will lease that address to the client. The address assignment process is identical for both IPv4 and IPv6 addressing. In the interest of consistency, the ports used are UDP 67 for the server and UDP 68 for the client.
– HTTP 80
Web Browsers use the Hypertext Transfer Protocol (HTTP) for internet communications and can be considered the foundation of the World Wide Web. It uses the client/server method where a client uses a Uniform Resource Locator (URL) to locate and request information from the target server of the resource. The response is more often than not an HTML page. A typical URL begins with http:// (or increasingly https://) followed by the Fully Qualified Domain Name (FQDN) of the desired resource. URLs to websites can be distributed between parties in messages containing the address which can be converted into clickable links called hyperlinks in reference to the hypertext communication being used. HTTP uses TCP/UDP port 80 and sends unencrypted data by default. This is inherently un-secure.
– HTTPS 443
The HTTP Secure (HTTPS) uses encryption protocols to secure HTTP traffic. Most commonly Secure Sockets Layer (SSL) or Transport Layer Security (TLS).
– SNMP 161
As one of the more popular network management protocols Simple Network Management Protocol (SNMP) is used to monitor and configure network nodes such as Printers, hosts, routers, and servers to name a few using a network manager on TCP/UDP ports 161 and 162. SNMP agent software is used on the nodes to enable monitoring.
– RDP 3389
OK, so this is for the old timers that had their Telnet then Terminal Services. From Windows XP onward the Remote Desktop Connection (RDC) was available. Using the Remote Desktop Protocol (RDP) on TCP/UDP port 3389, RDC is able to bring the fully functional remote machine’s desktop and programs to your device. This requires that the client and server software be configured on Microsoft products but versions are available for most OS’s. You can bring your home PC up on your iPhone.
– NTP 123
One of the oldest protocols Network Time Protocol (NTP) is used to synchronize the time on packet switched networks. Time synchronization is crucial to systems and processes the update data. If a program considers your update older than its latest it may be dropped.
– SIP 5060, 5061
The Session Initiated Protocol (SIP) supports VoIP and multimedia. It works with the IP protocol to create or terminate a session while handling any necessary changes. SIP relies on other protocols such as H.323 to ensure real-time delivery. The SIP protocol can be used as a unicast or two-party session as well as multicast or multi-party sessions.
– SMB 445
Server Message Block (SMB) predates Active Directory and was the foundation of Microsoft’s Windows for Workgroups networking capability. Based on NetBIOS it can run on UDP ports 137, 138 and TCP ports 137, 139 as NetBIOS over TCP/IP. It can also run directly on TCP port 445. While being one of the oldest networking protocols it has been continuously improved and the 3.0 version implemented with Windows 8 (3.02 in 8.1) supports improved performance in virtualized data centers. It is pervasive in many network applications and embedded devices. With newer versions supporting end to end AES encryption. There have been further advances in Windows 10 however, those are outside the scope of these exam objectives. You may also see this service as Common Internet File System (CIFS) or Samba depending on the operating system.
– POP 110
Receiving email is done over several different protocols. There are two main protocols available depending on your service. The first is Post Office Protocol (POP) with the latest version being POP3. This protocol uses port 110 by default and is responsible for the management of messages on the server (saving them or deleting). Deleting the message after delivery is the default mode. Leaving messages on the server is useful if you use multiple devices for messaging.
– IMAP 143
Today’s email user is likely to be using it on a collection of devices as opposed to the traditional PC. They have any or all of the possible devices, Tablets, Smartphones, or Laptops. All are Internet-connected and waiting for email. Now if your smartphone downloads and deletes a work-related email (POP3 default) you have a problem when you check email on your PC or laptop because it’s gone. The Internet Message Access Protocol (IMAP) on TCP port 143 solves this problem by leaving the messages on the server regardless of the delivery status. Every device that checks will get the email. This is great unless you get spammed a lot. Consider that it’s possible that 18 out of 20 of your emails are junk. Your server space will fill up quite quickly. This calls for closer scrutiny of the undeleted messages on your server. You have to move them to the trash folder and purge it or configure the client to purge trash. In spite of this, IMAP is the preferred client messaging protocol.
This is it for Part 1! Click here to go to Part 2/2.
Click here to go back to the Network+ ExamNotes Table of Content