A+ Exam Objective 4.2 Summarize aspects of client-side virtualization.
Click here to go back to the domain 4.0 table of content
Welcome to ExamNotes by CertBlaster! In this section, we will look at client-side virtualization, the ability to do more with less. Multiple tasks that once took multiple machines to perform can now be done by one machine’s processing power. This process is called virtualization and can involve two methods. Server-side virtualization (Type 1) occurs when all of the processing is handled by the server which in turn delivers virtual environments or machines to each client. Client-side virtualization (Type 2) occurs when the client desktops are virtualized into multiple machines. In both cases, the virtual machines operate in their own isolated space where their OS is installed on software that is used to emulate physical hardware.
The purpose of virtual machines
The purpose of virtual machines (VMs) is multi-layered. Primarily, virtualization maximizes the resources available. No additional physical resources are required for each virtual machine such as keyboards, mice, and monitors. This reduces energy consumption and also lowers overall heat generation. Another very stabilizing aspect of using the virtual environment is that since the entire machine is now essentially software, it is easier to back up and much easier to transport. There is no hardware to transport and only the set of files, including the VHD (Virtual Hard Disk), is required for transportation.
Virtual machines are run on software that emulates a customizable, physical hardware environment and supports the installation and operation of multiple operating systems. This is beneficial in application testing where a single physical machine can support Windows, OS X, and Linux systems, providing a reliable operational environment to evaluate the products. This configuration also enables the user to run an older application, for example, one that requires Windows XP, by installing it on a virtual Windows XP machine.
Sandbox
A sandbox is an isolated testing environment that allows content developers to deploy their projects without impacting the host machine. This can be accomplished using server-based sandboxes or using the user’s own desktop environment. Windows provides a sandbox for testing.
Note: The Windows Sandbox lets the user see the code and the result. However, when the Windows sandbox is closed, the contents are discarded and permanently lost.
Windows Sandbox is a valuable tool for developers since it confines the code to the sandbox without affecting the host system.
Test development
In a sandbox, developers are free to test their code and chase any bugs. Again, remember that nothing in the sandbox session is saved.
Application virtualization
Application virtualization allows an app to run on an operating system without having to install the app. The system accessing the Virtualized app behaves as if the app is running locally when in fact, the app is running on a server. By implementing a virtualization layer between the server and client, the app encapsulates the necessary environment that would be expected by the client through a single executable file. In fact, the client is oblivious to the substitution and operates as expected.
Legacy software/OS
Virtualization allows older legacy software and Operating Systems to run on newer systems without the compatibility issues that would normally occur.
Cross-platform virtualization
The ability to run app code on different platforms is accomplished through cross-platform virtualization. This method helps to develop apps that are compatible with major Operating Systems such as Windows, Android, and Mac varieties. Cross-platform virtualization is used in apps such as Bloomberg Anywhere, Facebook, and Instagram. These apps can be run on PCs or Smartphones by downloading and executing the appropriate version.
VMMs such as Microsoft’s Hyper-V, VMware, and Oracle can be used to create VMs.
Resource requirements
Resource requirements for hypervisors, or Virtual Machine Monitors (VMMs), depend on the scale, the number of virtual machines (or instances) to be deployed, the anticipated number of users, and the type of hypervisor being used. The VMM allocates a specified amount of Processor cores, memory, and hard disk space to each virtual machine instance. There must be sufficient resources to support the host operating system, the VMM, and the VMs to be deployed. VMMs like Microsoft’s Hyper-V, VMware, and Oracle can be used to create VMs.
Shown below is an example of a generous allotment of Processor, memory, and disk space that has been dedicated to a VM. Note the memory allocation and remember that the 64-bit version of Windows 8 only requires 2 GB of memory. The additional Processor, memory, and disk space can then be used to support more users. The VMM captures these resources when this example VM is running.
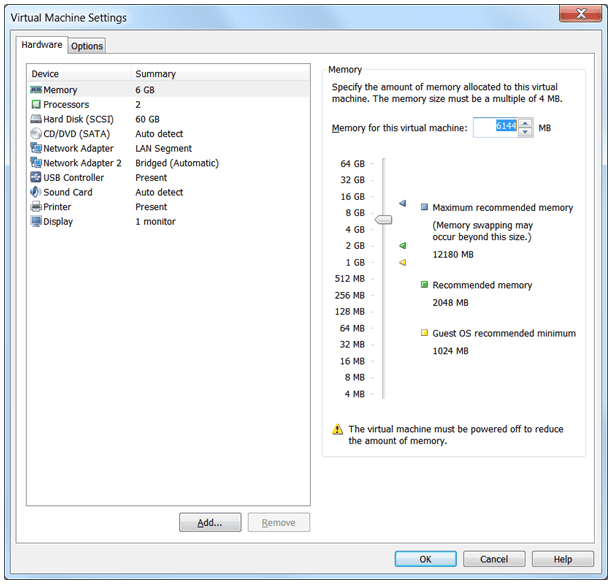
The VMM controls the total amount of memory available for all VMs while leaving sufficient resources for the host. You should not run a VM below its system requirements or above an amount that is supportable by the host as performance will suffer. This particular host has a 6-core processor and 16 GB of memory. With a host requirement of 2 GB and a 2 TB hard disk, there is plenty of room for a single VM instance. As you enable each VM instance, less computing power is available to the host.
Emulator requirements
One thing is constant: the host system’s UEFI/BIOS must support virtualization. Intel platforms use Intel VT and AMD platforms use AMD-V. Without these enhancements, virtualization on the host is not possible. The Emulator (VMM) must have access to enough resources in order to sufficiently cover the host OS and any resource allocations due to the VMs.
Shown below is the same VM running alongside a Linux installation that has 2 GB assigned. That’s 2 GB for the host, 2 GB for the Linux instance, and 6 GB for the Windows install which equates to 10 GB total memory usage.
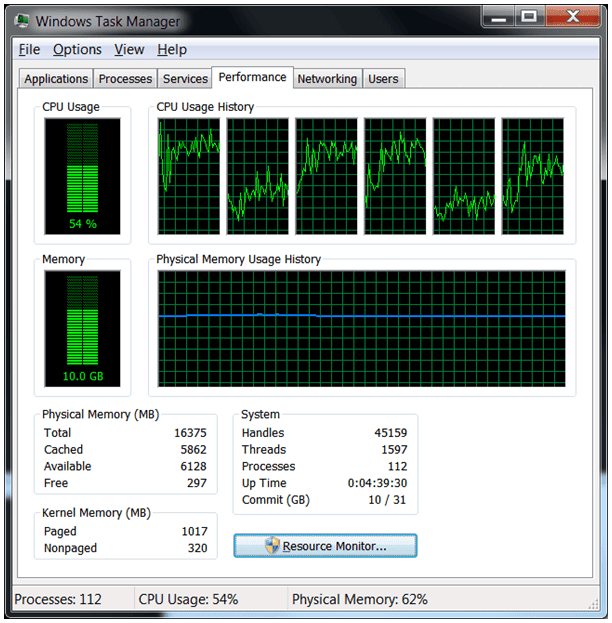
In comparison at rest with no VMM enabled, the machine uses roughly 30% of the Processor and 4.1 GB RAM.
Security requirements
Security requirements for VMs are particularly important because new users tend to think that VMs are protected by the host’s antivirus/antimalware software. This is not the case. Remember that virtual machines are completely isolated from the host. Install the proper protection packages on your VM and also realize that as a “machine,” separate software licensing applies in most cases. Read your agreement carefully.
Network requirements
On a hosted VMM, you cannot consume more network bandwidth than the host can support. For example, if you create instances of a Web server, an FTP server, and a file server on the host machine and the instances experience high network traffic, the host PC’s networking performance will fail since the network bandwidth will be allocated to the running VMs. If the network traffic is really high, the network performance of the VMs will also fail.
That’s it for 4.2! and that completes this very short Main Domain 4.0! See you in domain 5.

