A+ Exam Objective 2.4 Summarize services provided by networked hosts.
Click here to go back to the A+ Main Domain 2.0 Table of Content
Welcome to ExamNotes by CertBlaster! Here we will look at some of the specific services provided by network servers and other network hosts. We will examine the purpose and properties of various servers, internet appliances, and legacy systems.
Server roles
Specialized servers are the key to efficient web content delivery for mail, file print, addressing, and name services as well as user authentication. We will now break them down.
DNS
DNS servers have made user interaction on the internet dramatically simpler. DNS servers translate Fully Qualified Domain Names (FQDN) into IP addresses. Once a server performs this translation, the translation information is stored in its database for quicker access.
The DNS (Dynamic Name Server) is joined to the Dynamic Name System which allows it to consult with other DNS servers when necessary. A new server will do this frequently but over time, less frequently as it consults its local database first.
DHCP
A DHCP server is responsible for delivering IP addressing and related configuration information to its clients using the Dynamic Host Configuration Protocol. This service has saved countless man-hours and address duplications. The DHCP server uses an assigned address range, called a scope, in order to provide addresses to hosts without duplication along with any other necessary information such as subnet masks and gateway information. These addresses are leased to the host for a predefined period of time, after which they are refreshed or renewed.
Fileshare
A File server is primarily used to establish a central repository where users can store and share content such as documents, media files, and spreadsheets. The computer hosting the service is attached to the local network. A NAS (Network Attached Storage) device is often used in this type of application. However, this is not the same as an internet-based file server which uses the FTP protocol and is accessed using FTP client software.
Print servers
A Print server is a network-connected shared device that manages and distributes print “jobs” to the printers it controls. Users and administrators can manage print jobs through the queue, which displays all jobs received by the server and their status. A single user can manage their own jobs and an administrator can manage all jobs. While print servers as computers are still a part of many networks, stand-alone wired and wireless network-based printers exist that contain built-in print servers.
Mail servers
A Mail server can conceptually be considered an email server as it handles email. Email is customarily sent using an email client software package, which allows emails to be composed and sent. This same program will also check your mail server for any inbound messages. There are two main types of mail servers: incoming and outgoing. The outgoing server will use the Simple Mail Transport Protocol (SMTP) to send traffic to other mail servers en route to the destination. Delivery to the destination client is achieved using one of two incoming server types: POP3 (Post Office Protocol 3) and IMAP (Internet Message Access Protocol). To summarize, you send email using an SMTP-configured mail server and receive email using either a POP3 or IMAP server. These can be separate servers or hosted on the same server.
Syslog
Syslog is a protocol that allows network devices to send TCP messages to a Syslog server regarding network events such as logon/logoffs, errors, and maintenance. The syslog server maintains a database of these devices and events for use by administrators.
Web servers
A Web server is used by companies to deliver web-based content over HTTP. This can be done privately, in the case of an internally accessed company webpage, or publicly over the internet.
Authentication, authorization, and accounting (AAA)
For enhanced network security, the AAA model was established. This model may incorporate one or more servers or apps running on the that handle user authentication, authorization to use network resources, and accounting to provide records of the resources accessed by users. An example of one service is an Authentication server which is usually an application running on a server, such as Active Directory for example. This internet or network appliance handles authentication by providing a user, or device, access to designated resources on the network as determined by the administrator.
Internet appliance
Spam gateways
A gateway spam filter is a software solution for filtering email. Usually installed as an on-premises virtual appliance positioned behind the network firewall, an email gateway spam filter eliminates the vast majority of spam emails from the communication flow, ensuring clean emails arrive at their destination
Proxy server
A Proxy server is a dedicated computer or network device that handles all external requests made by users on the network. When the Proxy server receives a request for a webpage, it checks its internal cache of previous requests and if found delivers the content quickly, providing improved performance. If the content is not cached, the Proxy will either connect to or act as a firewall and perform private to public NAT (Network Address Translation). The Proxy is capable of masking the client IP address, blocking specified traffic, and filtering out malicious traffic.
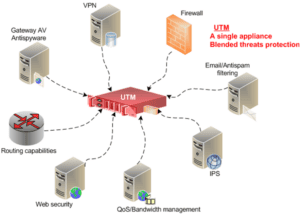
Unified Threat Management – UTM
Unified Threat Management (UTM) is a way to reduce cost and administrative overhead by combining multiple security features, such as routers, firewalls, and content filters, into a single hardware appliance in order to protect the network from unwanted or malicious traffic. The UTM is generally positioned between the Internet and the protected network. Here is a look at some of the possible elements.
Intrusion Detection System – IDS
The Intrusion Detection System (IDS) is one of the earliest network intrusion monitoring devices and is often found as a feature of a UTM, router, and server. It comes in two primary configurations, either as a network-based NIDS, that will monitor an entire network or as a Host-based solution HIDS when individual workstations have this capability. The IDS signals an alarm when suspicious activity is detected. However, this solution lacks the capability to block traffic.
Intrusion Protection System – IPS
An Intrusion Protection System (IPS) takes the IDS concept and evolves it to detect an alert condition before it enters the network and drops or blocks the connection. This is an effective approach but is not a replacement for IDS. The IPS is vulnerable to encrypted network traffic, making a layered approach the optimum solution as opposed to “either-or”.
End-point management server
Endpoints are any devices, such as computers, tablets, smartphones, and laptops, that require network access. The endpoint server inspects the endpoints to see if they meet the established policy criteria before they can access the network. Endpoint condition includes the status of software updates/patches and anti-malware updates.
Legacy / embedded systems
When considering network servers and devices, remember that you will encounter networks that are comprised of a mix of new(er) and legacy (= old) hardware. A single computer hosting multiple services, such as file and print or web and email, is not uncommon. Also, you will encounter services that are embedded in the firmware. Many routers, particularly consumer-grade or SOHO designs, have services such as DHCP and Proxy built in.
Supervisory control and data acquisition – SCADA
SCADA systems are used to control the performance and efficiency of industrial processes which, while being repetitive, require efficient operational control. SCADA has evolved from simple Programmable Logic Controllers (PLCs) that remain at the core of the system, to overall system control. Today’s SCADA uses a GUI to allow for monitoring functions, and the capability to capture and save real-time data.
Internet of Things (IoT) devices
IoT, where to start? The concept of the Internet of things (IoT) describes the many diverse things that can communicate and be controlled wirelessly using the Internet via a smartphone app. This technology is useful in business but your interaction with the IoT will probably begin at home. The technologies used in this operation will be discussed in the next article. For now, we’ll start with Wi-Fi and, Bluetooth.
The increasing availability of cellular and WiFi connectivity has led to an astounding array of connected devices. You will see practically everything in your environment having some degree of internet capability. Devices like doorbell cameras can be used to monitor activity at the premise from virtually anywhere, providing immediate security and a recording of any activities. Does your dishwasher require an internet connection? Some models do! The list goes on, Lights, thermostats, and heart/health monitors can all be controlled or monitored remotely.
The most common example of an IoT device is a Smartphone. A Smartphone gives a user the ability to talk, text, and send/receive data all in one compact package. A Smartphone also has a GPS receiver that’s accurate to within 100 ft. However, a connected device is always transferring data. For example, location services such as mapping apps are constantly tracking a user’s travels. Similarly, voice-to-text is always listening to any conversation. Every connected device carries its own security concerns so take the time to consider the risks vs. rewards when using a device.
IoT devices can be controlled directly through a smartphone or a voice-activated digital assistant. With the right equipment, a home thermostat can be adjusted, the doors can be locked, and the lights can be turned on through a smartphone or voice-activated digital assistant.
Home security has also benefited greatly from IoT devices. Besides locking the doors, motion-activated cameras with speakers can be installed to monitor for or even communicate with intruders or package thieves.
Lastly, a voice-activated internet-connected digital assistant can also help keep track of devices.
That’s it for Objective 2.4. Good Luck on the test. You are getting closer…
Click here to go back to the A+ Main Domain 2.0 Table of Content

