Welcome to Exam Notes by CertBlaster. In this edition, we will examine the topics in Network Plus N10-007 Objective 3.3 “Explain common scanning, monitoring, and patching processes and summarize their expected outputs.” Enjoy!
Log reviewing
Each time a device like a switch, router, firewall or the Webserver OS performs an action it records the activity in a log file. A good example is a honeypot log that reveals attacks and exploit attempts. That log file is viewable and stored in a central location using the syslog format. These files contain an enormous amount of information and require a lot of effort and concentration if they are being reviewed line by line. Fortunately, there is software available that allows you to view the information graphically. More on that later in SIEM. The important point here is that the logs be monitored and reviewed regularly.
Vulnerability scanning
Our networks are continuously under attack. Vulnerability scans are used to detect potential network weaknesses without taking any action. Your network can be tested for vulnerabilities by your internal IT staff. You can also use an outside party to perform vulnerability tests. To attempt to exploit any vulnerabilities discovered, the penetration testing process uses the available tools and utilities to simulate an attack, attempt an exploit. and determine the scope of the vulnerability. Consider vulnerability scans as a non-invasive action versus the invasive nature of a penetration test scan. Remember that there are constant exploit attempts and more importantly the hackers are using the same tools against you. The topics that follow describe some of the methods of detection and defense.
Port scanning
Open network ports on a system are examined by port scanning. You can scan for devices and open ports from the command line using the Nmap utility. Nmap can provide the information about the operating systems and services running on hosts. Third-party utilities provide more features and use a GUI.

Metasploit
Penetration testing tools like Metasploit are highly effective penetration testing tools. Metasploit can perform external network analysis, build and remotely control exploits. It also maintains a database of compromised devices. Pen tests performed by authorized parties is known as Ethical hacking. Another popular pen test program is Nessus. Nessus performs tests to seek unauthorized access to sensitive information. This is an effective tool for full analysis using real-time vulnerability updates enabling your team to identify and mitigate threats as they occur.
The software and operating systems are continuously being probed for weaknesses. When one is found Patch management software can be used to provide additional protection. After applying a software patch, you should run a security baseline to check your current results against the latest stored baseline.
Reviewing baselines helps you track the impact of your changes and review them for problems.
If you apply a patch that degrades your performance or security that patch can be uninstalled (Rollback) to neutralize any negative effects caused by the patch.
All actions on your network are logged. The log files can be analyzed individually, or they can be displayed graphically in a SIEM (System Information and Event Management) program.
Notifications can be issued by the SIEM as an alert and sent to the IT staff for investigation. Our example demonstrates a vulnerability scan on an unpatched OS.
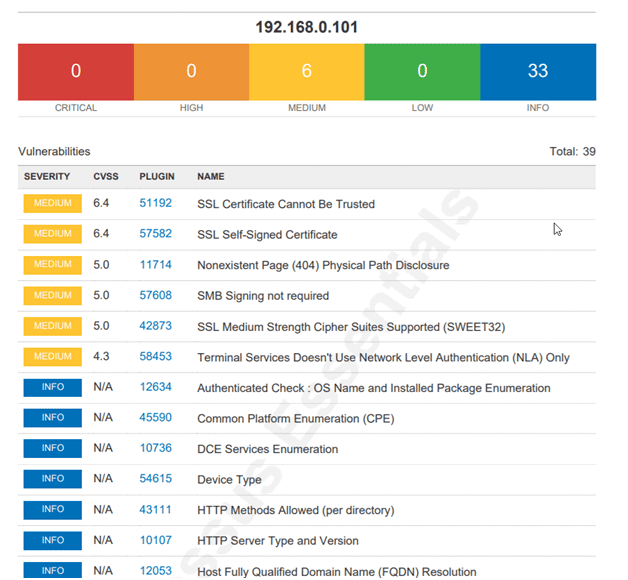
SIEM Monitor
When testing our performance metrics. The GUI output of SIEM and event management software provide real-time running graphical feedback on your operation. Your network can be tested for:
Error rate
The error rate is a metric that counts the packets that require retransmission. It is expressed as a percentage.
Utilization
This metric displays the actual throughput versus the bandwidth available.
Packet drops
When a packet is dropped it must be retransmitted. This takes a toll on network performance that increases as long as the condition exists.
That’s all for objective 3.3! See you in 3.4!

By continuing to browse this site, you accept the use of cookies and similar technologies that will allow the use of your data by CertBlaster in order to produce audience statistics- see our privacy policy.