Welcome to ExamNotes by CertBlaster! This edition will examine A plus 1002 Sub-objective 2.8 which covers mobile device security and how various systems and features can be used to enhance device security. Let’s get started!
Click here for the A+ Practice Test Bundle for A+ Exams 220-1001 & 220-1002
Energy saving and security are combined when deploying screen lock technology. In previous sections, screen locks were covered as they related to workstations. Mobile devices are more prone to being compromised or lost. In either case, mobile devices need to have stricter access requirements such as biometric or behavioral security features. Here, we will explore the additional features offered by screen locks on mobile devices.
More and more smartphones are being produced with biometric security features such as a fingerprint scanner. The user configures the device by supplying a fingerprint sample during the initial setup or later on in the Settings, under Lock Screen, and choosing Fingerprint. Editing this setting will require entering a passcode in order to prevent unauthorized changes. Next, supply the fingerprint sample by tapping the home button for the capacitive type reader until there are enough samples to satisfy the software. Be sure to supply enough samples to allow slightly off-center finger placement.
When enabled, the fingerprint lock compares the electrical impulses generated from contact areas on the fingerprint ridges and non-contact areas of the spaces between the ridges. Optical reader technology uses high-resolution imaging to capture the fingerprint. Once captured, the fingerprint is analyzed for the fine details of the fingerprint, such as the lines and features, and is stored for comparison. This type of reader can be undermined by an accurate high-resolution image or even a correct 3D replica of the fingerprint on a fake fingertip.

Fingerprint
While not specified in your A+ exam objectives, other biometric authentication methods include iris/retinal scanners and voice recognition.
The face lock relies on key facial features, captured by the device’s onboard camera, in order to grant or deny user access. Facial recognition software uses the geometry of key facial features in order to build a digital mathematical rendering of values represented in those features. Facial recognition uses values such as the distance between the eyes or the width of the nose. Distinguishing facial features are measured such as the cheekbones. Facial recognition software has come a long way and now can reliably compare an image to its database and provide a match. The software is less likely to be fooled by changes that would cause a human to improperly identify a face, such as a change in hair color, hair length, or even facial hair.
Swipe lock technology stores a user-defined swipe pattern that will allow device access. This pattern can be as simple as a straight swipe in any direction or something more complex. It is recommended that the swipe pattern should be followed by a second form of authentication. Use either a passcode or facial recognition to fully access the device.
A passcode is an acceptable security method and it is best to use one that has at least 6 non-consecutive or non-adjacent numbers. This method is always stronger as a part of multifactor authentication when used with other methods.
In the event that the mobile device is lost or stolen, the capability to remotely delete all of the data on the device is extremely important to the device’s security. In most cases, the security measures described above will be sufficient to secure the data. When it is fairly certain that the device cannot be recovered or that the security measures will not withstand a breach, there is no choice but to clear all of the personal data from the device. This operation will return the device to its factory settings. The remote wipe program we use does not have the capability to clear data from SD cards that may be installed on the device. Some apps are capable of this feature and if this risk exists, select the remote software accordingly.
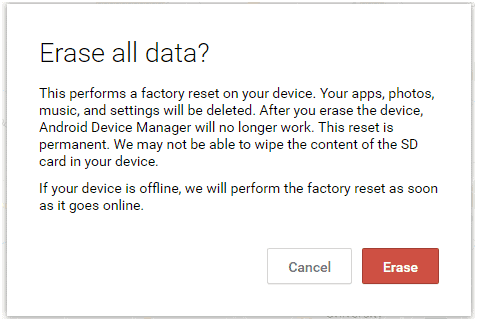
Remote wipe
If a mobile device has been misplaced, all mobile operating systems support a degree of interactive device location. The Android Device Manager for the Android OS uses Google Maps and the location information last reported by the device in order to provide the last known location. In some cases, this may be sufficient to find the device by finding the last location and activating the ringer. This particular application allows the user to ring the device, lock it, or remotely wipe the personal data, returning the device to its out-of-the-box configuration. Remember that the remote wipe feature and the locator apps will not work if the service is powered off or has its SIM card removed.
Shown below is the Android Device Manager which has located a misplaced device on the map and is ringing the phone.
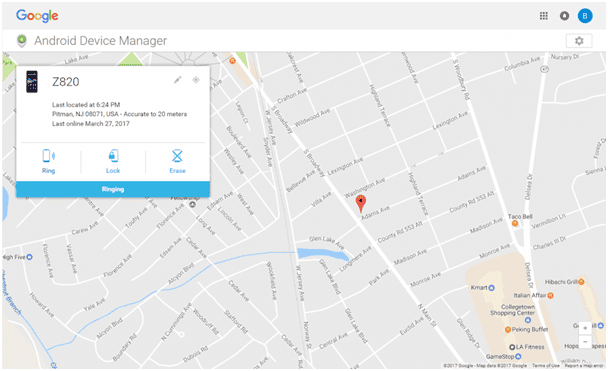
Device locator ring
Each mobile operating system supports backups to the Cloud. Examples of backup services include iTunes and iCloud for Apple devices, OneDrive for Microsoft, and Google Drive for Android. Access to these storage locations is controlled for the most part by email-specific logins. For example, a [email protected] account would be needed for Microsoft, [email protected] for Android, and a personal email (and a new password) for Apple and other free backup and storage locations such as Dropbox.
Click here for the A+ Practice Test Bundle for A+ Exams 220-1001 & 220-1002
All free backup services have either feature limitations, size limitations, or both.
iCloud is geared towards storage while iTunes handles backups and synchronization. All files and folders added to the local home directory of these apps. are maintained.
Note that all files added to the Dropbox folder are encrypted and synced immediately and automatically. Once the sync has completed, the files will be placed in encrypted storage online in two locations as well as being shared locally and on any shared devices. Shown below is a Dropbox upload featuring the sharing option in the alt menu, allowing specific items to be shared with other parties. Local content that has been synced is displayed with a green checkmark in the local folder. Local content in the middle of the sync process is shown with a blue circular icon.
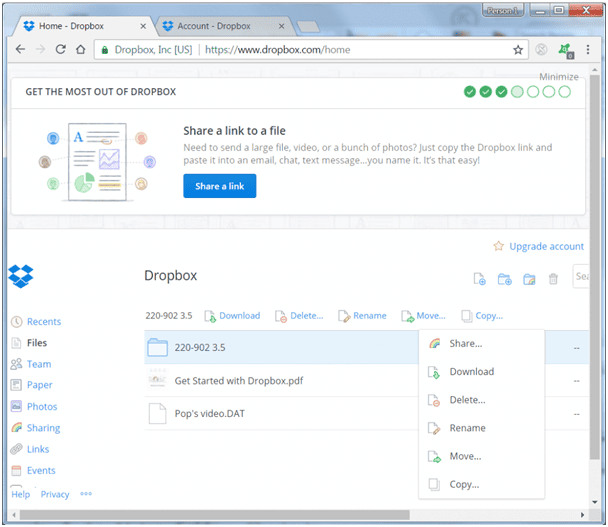
Dropbox sharing online
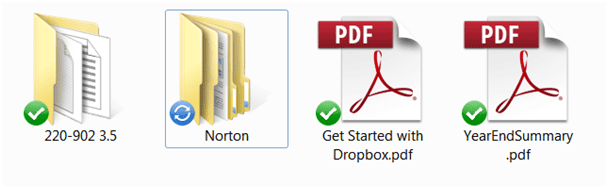
Sync confirmed upload in process
Failed login attempts restrictions
Mobile devices can be configured to lock after a specified number of login attempts. This is usually a temporary condition providing the user the time necessary to remember the password. In the conventional PC environment, it is common to see login restrictions such as the number of failed attempts that are allowed before the account locks. The number of attempts allowed can be reset. It is important to know that on an iPhone for example, after an excessive number of attempts the device will permanently lock and erase all data. In most cases, access can be restored by using the primary account and password data, providing of course that the device has not been erased.
So you think your smartphone or tablet is immune to malware and virus infection because the operating system is not commonly a target? Think again. While a virus is a rare or non-existent occurrence in the Android environment, malware propagates freely. Remember the distinction between a virus and malware. A virus’s main objective is to replicate itself by piggybacking in or on a seemingly benevolent file. When the host file is opened, the virus will replicate according to its programming.
Malware on the other hand describes all malicious content including viruses. The objective of most malware is two-fold. The first is secrecy. The longer the malware can exist, the more effective it is by virtue of the second point described here. Second, the majority of malware will generally not harm the host. There may be a performance impact due to the malware’s activity, but the bulk of malware programs will gather personal data, credit card information, login data, and keystrokes without disabling the device. Ransomware is the exception here in that its first operation is to lock and often encrypt the local data.
So what is the defense against this? Install a free or paid version of a trusted Antivirus/Antimalware suite. Select a widely known and respected package, check the reviews, and most importantly be absolutely certain the program is being downloaded from the correct source (see below under “Trusted sources vs. Untrusted sources.” Next, keep the detection definitions up to date. One of the main differences between the free and paid versions of antimalware programs is illustrated in the Malwarebytes program. The free version requires the user to update the definitions manually while the paid version does this automatically. Manual updates require discipline on the user’s end and can lead to conditions where newly discovered threats go undefended. Evil does not take days off!
Shown below is a popular program that would provide protection normally but may or may not since the databases are out of date.
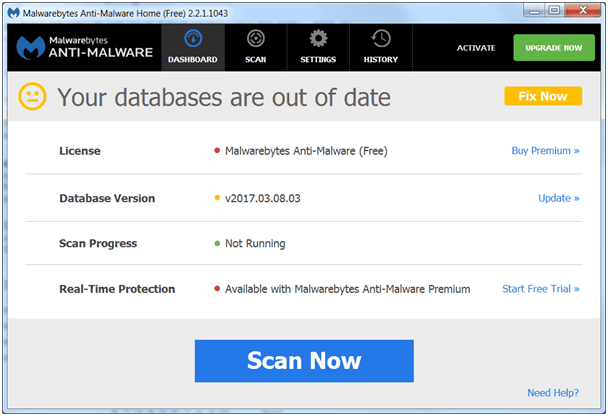
Outdated Antimalware definition database
A patch modifies existing software in order to add security features or operational improvements, also known as bug fixes. Critical patches are known as hotfixes. A Service Pack refers to a group of patches and hotfixes that have been compiled into a single download and are installed as a cumulative update. OS updates are, as the name implies, updates to the OS.
In the mobile environment, device programming is being constantly tested for vulnerabilities. As important as it is to keep the device’s virus and malware protection up to date, it is equally important to allow the mobile OS to patch and update its software. As we covered earlier, hardware requires some form of software to operate properly. This could be embedded firmware or software drivers. In the case of firmware, it is more likely to be exploited as opposed to being altered. A widely used technique to trick users into installing malware employs a fake download site loaded with malware-infected drivers.
As referenced earlier in this section, multifactor authentication is becoming more accessible to the average user. Before, iris/retinal scanners and facial recognition authentication were only found in the corporate realm. Now, it can be integrated into the majority of mobile devices.
Encryption is a highly effective security measure for files, folders, and even volumes. Encrypted content is essentially digital junk without the decryption key. However, this enhanced security comes with a system performance penalty. The solution to this performance impact is whole device encryption which encrypts everything, decreasing any internal operational performance lag.
The combination of more than one authentication method is called multifactor authentication. Smartphones or other mobile devices can play an integral part in this process. Multifactor methods are frequently used by financial institutions in order to prevent unauthorized access and intrusion. Some multifactor authentication implementations use an email/password combination in order to initiate a callback or text back passphrase delivery. This is usually a one-time passphrase (OTP) that is delivered to the mobile device which is then used as the second element of authentication. When mobile device connectivity cannot be assured, the multifactor method can utilize an email/password combined with facial recognition in order to provide the necessary security level.
As a rule, the more sophisticated the authentication method, the less likely it is to be included in a standard mobile device configuration. This is due to the need for minimal software loads on standard device implementations as additional apps are installed as needed.
Authentication apps are widely available. For individual security, a highly rated freeware app such as Google Authenticator or Microsoft Authenticator will be sufficient.
In the business environment, the app must be able to be implemented across many platforms. It will need to be tested in the environment in order to reveal any weaknesses. Shown below is a look at some of the highly-rated free authenticator apps.

Authenticator Apps
Software drivers and other apps can easily be corrupted, allowing malware to operate. Study any system errors and verify the source of all errors and warnings. Once satisfied, always start with the manufacturer’s recommended website when updating any elements of the system. This is Google Play for Android, Apple’s App Store for iOS, and the Microsoft Store for Windows-based devices. Use the device’s settings whenever possible to block or restrict unknown or untrusted sites. It is necessary to examine the actual sources of everything installed on the machine. Given the possibility of misdirected web traffic, look at the URLs carefully. It’s essential to understand the importance of using trusted sites to obtain software. Furthermore, know the consequences of installing untrusted content which include identity theft and complete device failures.
On a mobile device, some features of the firewall are configured during individual app installations. Each app requests specific permissions before installing. Review these permissions for their relationship to the app operation and determine if they should be granted.
For example, a weather app that requests location information for its installation is more justifiable than a text-to-speech app that needs access to the camera. This feature requirement is usually an all-or-nothing selection. Ultimately if you do not agree to all permissions the app requests, the app will not install. There are many apps to inspect and install but there is only one set of personal banking credentials (yours) to be compromised. Err on the side of caution.
The term BYOD (Bring Your Own Device) describes a corporate policy that allows an employee to use their own device in the corporate environment. This policy includes device evaluation by the company’s IT department to ensure the device meets the corporate security requirements regarding software, patches, antimalware, firewall, VPN, login requirements, and encryption. Any software installations needed to meet the BYOD policy are referred to as on-boarding. Corporate-owned devices are configured to meet these same requirements.
Click here for the A+ Practice Test Bundle for A+ Exams 220-1001 & 220-1002
The profile security requirements described above may involve additional components such as cloud backup capability. This policy will be clearly outlined and enforced. This policy will also include provisions for wiping the data from lost/stolen devices or provisions for employees that have been dismissed. That’s all for 220-1002 objective 2.8. If you have been following these posts consecutively, you are getting towards the end of domain 2.0. Good luck with the test!

By continuing to browse this site, you accept the use of cookies and similar technologies that will allow the use of your data by CertBlaster in order to produce audience statistics- see our privacy policy.