Welcome to ExamNotes by CertBlaster! This edition will cover objective 4.1 Compare and contrast best practices associated with types of documentation. In this section, we will cover the ideal methods for documentation. Dig in!
Click here for the A+ Practice Test Bundle for A+ Exams 220-1001 & 220-1002
All IT departments should have and maintain network topology diagrams which depict current mapping information and connected devices. In the example shown below, observe that all of the devices encountered, such as Cloud resources, VLAN trunks and switches, routers, firewalls, and hosts, will be depicted in the network topology diagram along with their connection types, status, and addressing information. Note that all the addressing information is clear and up-to-date. You can see a problem in the 192.168.60.0 /24 subnet at the upper-left. Hopefully you will start out on a smaller scale!
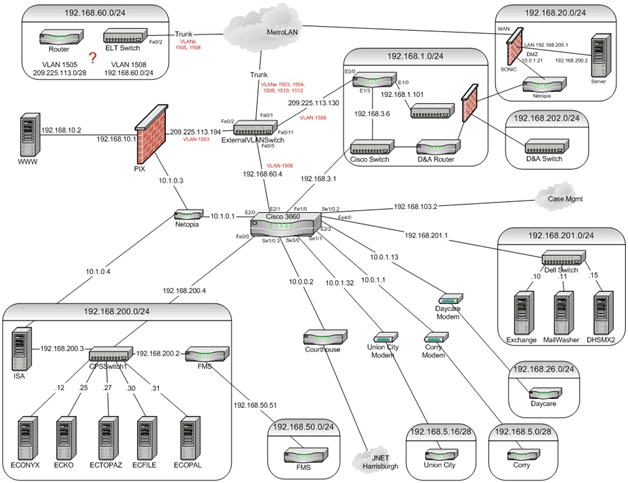
Network topology
A knowledge base refers to a collective repository for all pertinent information about IT operations. When an IT technician finds or troubleshoots a hardware or software issue, they should update their findings within the IT department’s knowledge base. They should also include installation and configuration details. This will help the IT department resolve recurring problems and help train new personnel.
Every organization is required to adhere to the laws, regulations, and policies relevant to their industry. Collectively referred to as the regulation and compliance policy, this policy will be tailored to the organization’s responsibilities. Maintaining compliance can be quite complicated and generally requires an individual or a whole department. As an IT technician, you will be expected to be aware of and follow the policies and guidelines in order to maintain compliance. Part of your organization’s onboarding process will include training in this area.
Most employees will need to consent to an Acceptable Use Policy (AUP) as part of their hiring and training process. This policy will clearly define unacceptable practices for employees and will describe activity prohibited on company devices such as viewing objectionable content, unauthorized software installation, and even online shopping. Violation of this policy can be grounds for termination!
Password policy
The password policy covers the organization’s best practices regarding passwords. The policy will cover password length, special character requirements, expiration, and reusability.
Any incident involving the violation of the AUP or any policies will be investigated internally and documented. Always report suspicious activity to your immediate supervisor and follow their instructions. Keep any evidence intact and document your observations clearly.
Corporate inventory should be monitored and controlled in order to allow tracking of valuable equipment within the organization. There are a few ways to accomplish this. Generally, Asset tags are affixed to computers and monitors. These tags are tamper resistant and can be tracked using asset tracking software. The tag will identify the company (owner) and have Barcodes that can be used with asset tracking software. RFID tags can also be used, allowing for a greater chance of recovering stolen equipment.
Click here for the A+ Practice Test Bundle for A+ Exams 220-1001 & 220-1002
That’s all for objective 4.1. See you in 4.2! Good luck on the test!

By continuing to browse this site, you accept the use of cookies and similar technologies that will allow the use of your data by CertBlaster in order to produce audience statistics- see our privacy policy.