Welcome to ExamNotes by CertBlaster! In this section, covering A plus 1002 Sub-objective 2.6 we will examine the security settings on a basic Windows OS installation. We will also discuss the differences between settings that are context-sensitive. When going through this section, please remember that we didn’t create the operating system. We only authored this guide.
Click here for the A+ Practice Test Bundle for A+ Exams 220-1001 & 220-1002
In order to manage permissions, Microsoft uses User accounts to assign rights and privileges. User accounts can also be assigned to a Group, containing multiple users and is assigned a specific set of privileges that apply to all users within the group. A user can belong to more than one group. Privileges explicitly assigned to an individual user take precedence over any conflicting group settings. Shown below is a look at the built-in groups in Computer Management.
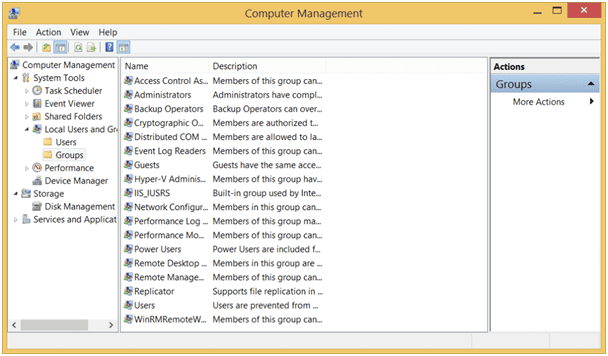
Local Users and Groups – Groups tab
The most powerful group is the Administrators group. The most powerful user account is the Administrator. Users assigned to the Administrators group have complete and unrestricted access to the computer and domain if applicable. Standard users can be temporarily elevated to Administrator status by temporarily using the alternate credentials, described later in this section. Best practice indicates that the actual Administrator account be disabled. This will affect only the Administrator account and not the Administrators group.
Within the user account hierarchy, the Power User has limited administrative powers but still has more than a standard user. The Power User group is included in current Windows operating systems in order to provide compatibility with legacy Windows versions such as XP and earlier.
The Guest account is limited in its capability since it can only create or modify objects in the guest account folder structure. The Guest account cannot make any changes to any files or folders elsewhere on the PC.
The Guest account is disabled by default. Enabling the account can be accomplished by clicking its icon on the login screen or by accessing Local Users and Groups in the Computer Management window in Control Panel > Administrative Tools. Even though the Guest account is a restricted account, please password protect it. Shown below is the Guest account page showing the default settings.

Guest account disabled
The Standard User account provides the best balance between privilege and security. Identified in the system as simply “Users,” Standard Users are allowed to run applications, perform common actions, and access most areas of the system without the need for administrative intervention. Activities that require access to system components, such as adding hardware or a software program, will trigger a UAC prompt and in some cases will require the administrator password. When Standard User accounts are created, Windows will ask if a child will be using this account. If so, use Parental Controls (Windows 7) or Family Safety (later OS versions) to rate, monitor, and restrict the account.
New users are created as Standard Users by default.

Set Standard User
NTFS and Share level permissions both provide a customizable level of security. Share level permissions are set on the share by the owner. NTFS permissions are set as a security property. NTFS and Share level permissions differ in some key aspects.
Click here for the A+ Practice Test Bundle for A+ Exams 220-1001 & 220-1002
Share permissions manage access at the folder level. In contrast, NTFS allows every file to have individual and varying accessibility if desired. Share permissions are used for compatibility with the FAT32 file system and support three permissions: Read, Change, and Full Control. NTFS can manage these attributes as well as others including Write, Modify, Read, Execute, and Special. There are instances where share permissions and NTFS permissions are essentially the same, such as Change in share and Modify in NTFS. Since both permission types are independent and their values are combined, the more restrictive combination is applied in order to determine permissions. This is in contrast to an NTFS to NTFS cumulative result which is less restrictive.
Allow versus deny can be interpreted as allow versus not allow. The deny permission is the strongest and will take precedence regardless of the weaker permissions applied. A group can be granted access to a folder and in NTFS, a specific user or users in that group can be given a deny permission. In this case even though the group is allowed access, that particular user’s deny permission overrides all others.
Moving content from one location to the other can be accomplished through several ways including from a command prompt or simply by dragging and dropping. The method used should be determined by the desired result. Should the content exist in both the source location and the destination? Should the content be removed from the source and exist only at the destination. As expected, copying the content results in the file being present at both locations while moving the content results in the file being only present at the destination. The command prompt allows files to be copied using the Copy command, files and folder structure to be copied using the Xcopy command, and files and folders to be copied using Robocopy (the newer, faster replacement for Xcopy). Both Xcopy and Robocopy retain the content’s permissions when using the correct syntax. For those who wish to use the GUI, transferring files is as simple as dragging and dropping, then choosing Move or Copy when the option menu pops up.
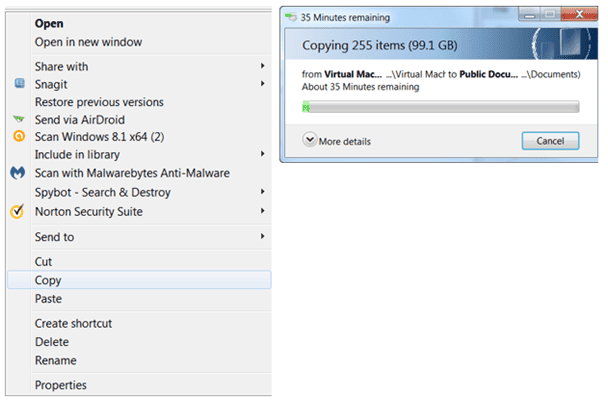
Copy Operation in GUI
Cut and Paste can also be used similarly. Right-click on your source object (file or folder), choose Cut or Copy, and then right-click and click Paste at the destination. Remember that for an NTFS source, the destination file structure must support NTFS otherwise the source permissions will be lost. When copying/moving NTFS to NTFS on a different volume, the file or folder will receive the cumulative permission set. This means that the permission sets will be compared and when a conflict exists, the least restrictive values will be used.
Operating systems including Windows indicate an object’s attributes in their file structure using one or more of these alpha designations.
Here is a list of them with a brief description.
A = Archive: This attribute is used by backup programs and other utilities to indicate that the file is ready for backup (archiving). After a file has been backed up, the Archive bit(value) is set to zero or off. If a program makes a change to a file, it will reset the bit to one indicating the need to include it in the next backup. This setting makes incremental backups possible by only archiving objects that have changed.
D = Directory: This setting indicates that the object is a directory, not a file.
H = Hidden: This setting indicates that the object is hidden from normal view. System files and folders are routinely hidden. In the GUI, the View setting will allow these files to be shown. When displayed, hidden files will be gray to visually differentiate it. A user may not be able to access this content without the administrator’s help.
I = Not Content Indexed: This setting indicates that the object is not indexed. Indexing, which is off by default, allows the operating system to perform faster searches. Objects that have this bit turned off will be included in searches.
R = Read-Only: This setting indicates that the object cannot be altered without resetting this value to off. Interestingly, Read-only protects a file from being altered but does not protect it from deletion.
S = System: This setting indicates that the object is a system file or folder and coupled with the read-only setting, prevents tampering. Do not delete or modify these files.
There are two types of shared folder objects: administrative shares and local shares. Local shares are created by users and are accessible by those with the appropriate permission. Administrative shares are generally used by administrators to access system drives and areas that are not generally shared. All four administrative share names are appended by a $ while the local share has a common name.
Permission propagation occurs when a container object (folder) is shared by its owner. Upon sharing, the owner can determine how much of the folder’s contents will receive the same set of permissions. This will affect how the files and folders within the container are treated by the OS. When applying permissions, there will be an option to apply the permissions to the containers, folders, subfolders, and files.
Inheritance describes the way permissions are handled within a shared folder. Depending on the settings, the Child folders, subfolders, and the original share folder may or may not receive the permissions applied to the Parent folder.
System files and folders are always classified as Read-Only and are usually hidden. Doing this helps protect the system from deliberate or unintentional damage. Standard users never see these files and folders, thereby keeping everything safe. Shown below is a hidden system folder and its properties. Note that the folder in question is grayed out. That’s the first sign to stay out. In the properties, notice the read-only setting which applies to the files in the folder. (Show Hidden System Folders)

Hidden System Folder Properties
Single Sign-On (SSO) identifies the practice of permitting a user and their programs to use a single set of credentials to automatically log into permitted sites and services. This saves the user the trouble of entering their login information for each website or secure location they visit. A good example of SSO is a Microsoft account. If the same login is used, each device will share access to different online accounts such as online storage and email.
A standard user, as a member of the Users group, is allowed a useful but limited level of activity. For example, there may be programs that require direct disk access or other system level operations that are outside the scope of the standard user. Using the runas command, with the user name and program name, at the command prompt will elevate the user’s privileges to administrator. This can also be accomplished by right-clicking the program’s icon or the Start menu shortcut and choosing “Run as Administrator.” Attempting to run a program that requires administrative privilege will result in a UAC and possibly require a password.
BitLocker Drive Encryption is a data protection feature that is used to encrypt the data on an entire disk. This encryption feature uses the host machine’s motherboard in order to develop the encryption method. BitLocker will not decrypt the disk without the TPM chip which is hardwired to the motherboard. On systems without a TPM chip, a portable USB key is produced during encryption and can be used to decrypt the contents of the drive.
Bitlocker-To-Go is BitLocker for external and portable devices. Since it is portable, the TPM chip is ignored in favor of a password. The password should be saved either to a local drive or by printing it. Bitlocker-To-Go was introduced in Windows 7. Earlier versions of Windows will be able to read from the portable device but will not be able to write to them.
In order to encrypt specific files and folders without using whole disk encryption, NTFS offers the Encrypting File System. Access the properties of the folder or file you wish to encrypt and check the “Encrypt contents to secure data” box.

Advanced EFS Encryption
That’s all for Objective 2.6! Hope you enjoyed it and hope you solidified your skills a bit. Good luck on the test!
Click here for the A+ Practice Test Bundle for A+ Exams 220-1001 & 220-1002

By continuing to browse this site, you accept the use of cookies and similar technologies that will allow the use of your data by CertBlaster in order to produce audience statistics- see our privacy policy.