Welcome to ExamNotes by CertBlaster! This edition brings us to A plus 1002 sub-objective 2.4 where we will discuss how to detect, remove, and prevent malware using appropriate tools and methods. These threats are not operating system specific (unless noted) and can affect most platforms and circumstances as you will see. You will also see the cost of non-compliance with policies or practices. Here we go!
Click here for the A+ Practice Test Bundle for A+ Exams 220-1001 & 220-1002
Malware is a generalized term that describes anything that intentionally causes harm or damage in the operating environment. The symptoms encountered due to Malware are often clues to the type of attack being fought. The items listed below categorize these attack types.
Ransomware is a malicious program that blocks access to the system and the data until a ransom is paid. Ransomware can be installed on the system by accessing an infected or compromised website, downloading a malicious file, or opening a malicious email attachment or hyperlink. A pop-up may appear that informs the user of a block and includes instructions on what to do next. The block may look like it is from a police or law enforcement agency. Newer ransomware infections can even modify the MBR and/or encrypt the hard drive contents (crypto-ware).
In order to unlock the computer, an amount of money must be paid in the specified anonymous manner and the user must hope that an unlock or decryption key is sent. Immediately power off the machine upon discovery of ransomware since it takes time to encrypt the files. This will lessen the impact of the encryption.
Trojans are fundamentally infected versions of real files. Be careful with what has been downloaded and scan it before it is opened or installed. This is particularly important when dealing with email attachments.
Trojans are designed to do any number of things. Trojans can delete files, compromise system information, and even grant access and control of the machine to the perpetrator. The symptoms of a system infected by Trojans include poor performance, increased or bogged down network and/or servers, and generally unpredictable behavior accompanied by new or deleted files in the system which often cause system failure.
KEYLOGGER
Rootkits are a particularly sinister malware variant. A rootkit infects a computer and grants the rootkit’s owner privileged access to the target PC without the user’s knowledge or consent. The defense against rootkits is to always keep the protection software up-to-date and to apply any and all security patches to the OS. Rootkits are usually well hidden and undetectable by conventional means. There are Rootkit detection packages available but rootkits are often hidden inside system files where detection is impossible. This makes prevention the primary defense. Download only from trusted sources and be cautious of emails from unknown sources.
New virus attacks are practically a daily occurrence. Viruses infect the system with the desired malicious payload and also replicate themselves onto connected devices. Viruses can spread over a network or through infected writable devices that are shared. Always write protect a USB thumb drive before inserting it into a system lest it becomes infected. A virus will reveal its presence on a system through increased network activity, sluggish system performance, or possibly by tricking the unsuspecting user with a false warning similar to the one shown below. If you ever see this message, DO NOT click okay and certainly DO NOT call anyone.
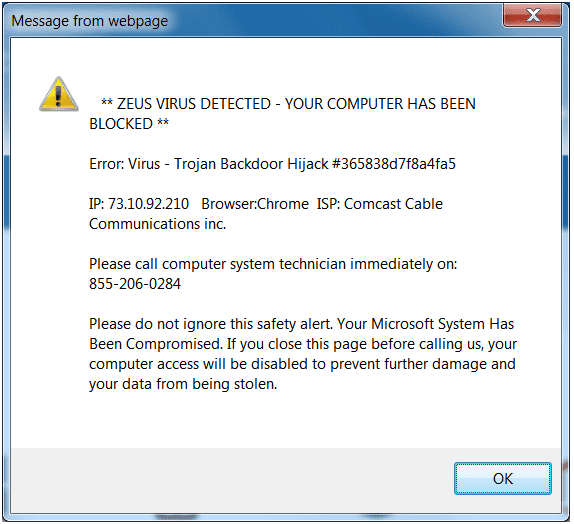
False warning
If you encounter this error message, use Ctrl-Alt-Del to launch the Task Manager or Command-Option-Esc on a Mac to launch Force Quit and kill the browser instance(s). If that fails, power off the system immediately. Then reboot and perform a virus scan immediately. This is a typical malware trick. If you agree to the false warning message, you will be asked to install harmful software under the guise that it will help clean the system. If you call the phone number, you will ultimately be asked to allow the technician to take over your machine.
Click here for the A+ Practice Test Bundle for A+ Exams 220-1001 & 220-1002
A symptom of virus infection is the inability to reach anti-virus and anti-virus sites. Norton, Symantec, and McAfee programs will not be able to reach their servers nor will you. Shown below is an anti-malware program that is unable to connect to its update server. Note the unable to access message in the white field in the screenshot below.
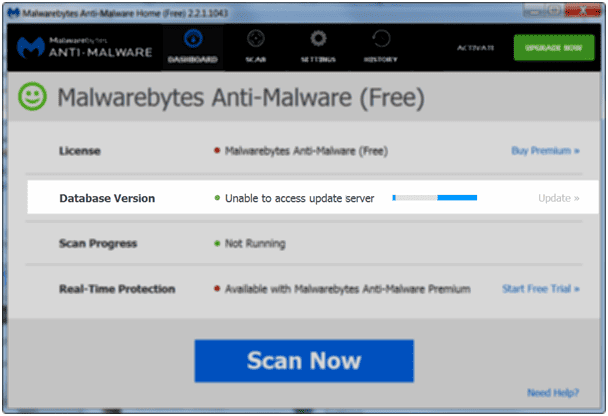
Server access fail
In the worst case, even the built-in safeguards are unable to update. Shown below is a Windows Defender update attempt on an infected machine. Note the progress after an hour and a half. Although it has not failed officially, the update is not going to finish.
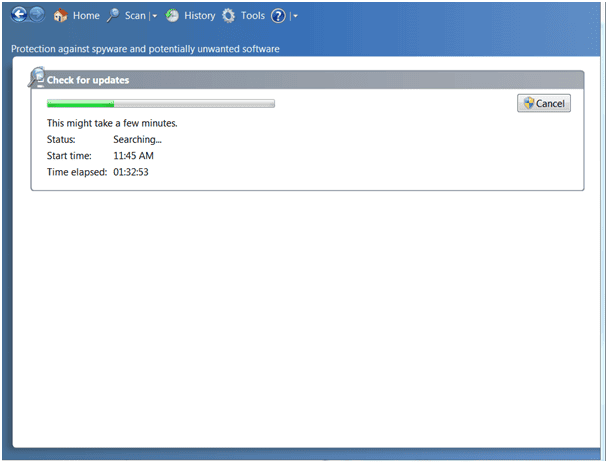
Defender update failure infected machine
When discussing a Zombie and its relationship to a botnet, picture an army of zombies. In addition, imagine your PC as one of potentially millions of PCs infected with the same malware that is commandeered by a single host. The entity that controls the botnet can literally use the infected machines towards a single purpose such as DDoS, Spam, or Malware distribution. Hundreds of billions of dollars in losses/damage can be attributed to botnets.
Worms attack connected devices and other network hosts by exploiting vulnerabilities in the operating system. Compared to Viruses and Trojans, a Worm will consume network bandwidth and overload network servers. The primary purpose of a Worm is to replicate itself to every possible node on a given network. Upon suspicion of a Worm infection, disconnect the computer from the network and/or Internet. Running the antivirus program after booting to a repair disk or into Safe Mode will help. In order to prevent this type of attack, keep the protection signatures up-to-date and avoid opening odd email attachments.
Spyware is software that is installed on a device without the consent of the user, collecting user data and sending it to a third party. These programs can monitor and record keystrokes, browsing information including login data, credit card numbers, and passwords or PINs. Confidential information can easily be compromised. It is important to have adequate defenses. Built into Windows is Windows Defender, offering real-time protection and background AV scanning.
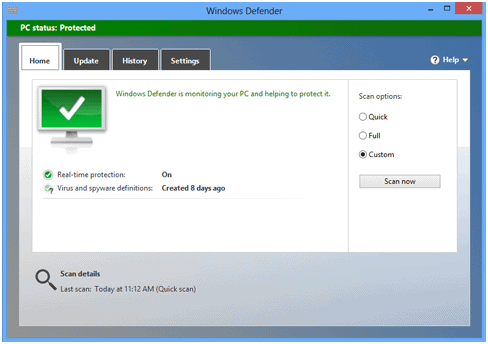
Windows defender
A layered approach can be considered when dealing with malware. This type of protection is also available in paid or premium versions of protection packages. Be careful when selecting products for system defense as programs commonly installed with the OS can conflict with purchased protection products. Also, avoid freeware that is unfamiliar as some programs are “wolves in sheep’s clothing” and contain malicious payloads.
Antivirus/antimalware
The best way to repair an infected machine is by booting to an antivirus repair disk or USB Drive. This process allows the system to boot to the repair media and to thoroughly scan the system before any system files or malware programs have a chance to launch. If a repair disk hasn’t been made, make one now. In the absence of a repair disk, scan the system in safe mode with the primary AV solution. Here is a look at Norton 360.
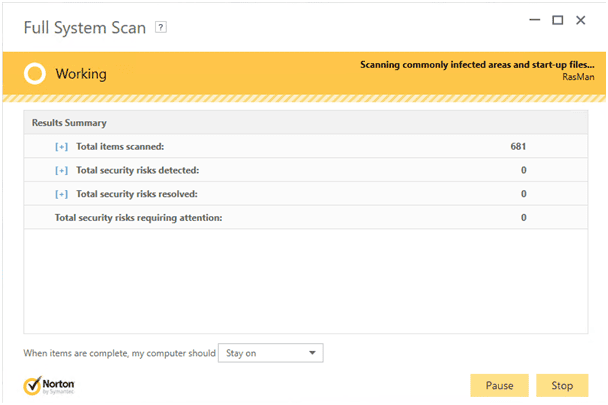
Norton Full Scan
Norton 360 was supplied by the ISP, no doubt to address their inability to control the issue (sorry, Norton is an added value!) Whenever possible, perform a Full scan. Scan as much as possible. Browser files and Temp files are hiding spots for malware so ensure these locations get checked. If a scan is going to be performed, do a full scan as opposed to a quick one.
A layered approach can be considered when dealing with malware. This type of protection is also available in paid or premium versions of protection packages. Be careful when selecting products for system defense as programs commonly installed with the OS can conflict with purchased protection products. Also, avoid freeware that is unfamiliar as some programs are “wolves in sheep’s clothing” and contain malicious payloads.
Recovery console
The current Windows RE replaced the recovery console and provides additional features to repair the system. For systems with startup problems, the updated F8 boot menu will provide options and allow access to the Advanced startup options shown below. For functioning operating systems, use the Control Panel > Recovery option and choose Restart now under Advanced startup. This grants access to the Command Prompt, Restore from a restore point, System image recover, and Startup settings.j
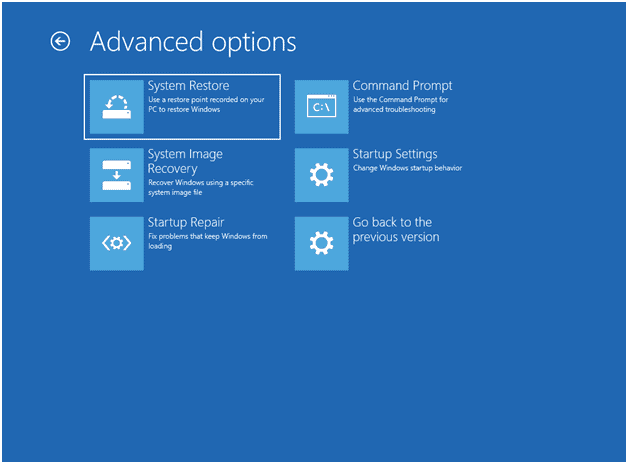
Advanced options
Backup/restore
In addition to File History, Windows 10 retains the Windows 7 backup and Restore utility which allows backups and system images to be stored on another disk or on the network. When needed, these backups can be restored to their original locations. This utility can also create a system repair disk.
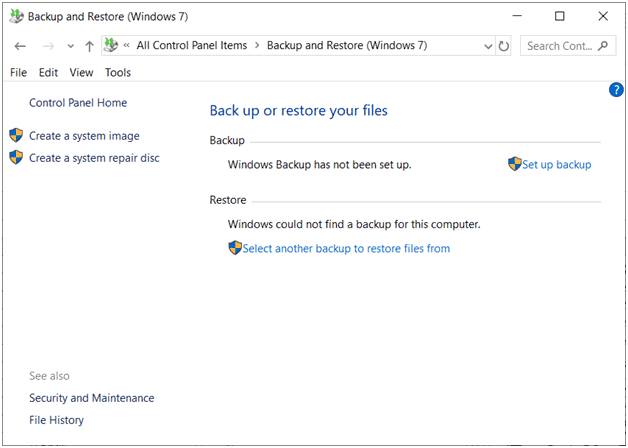
Backup and Restore
End-user education
The end-user is considered the weakest link in any protection plan. It is extremely important to make the end-user aware of the threats to their system. Always take time to explain the cause of any problems you have resolved. Give the end-user tools to protect themselves. Something as simple as hovering the mouse cursor over a link in order to view the actual web address can easily prevent an infection. Make sure the end-user knows how to update their A/V program as well as their operating system. Show them how to set schedules for these updates if necessary.
Click here for the A+ Practice Test Bundle for A+ Exams 220-1001 & 220-1002
Software firewalls
Windows Defender Firewall provides good protection for PCs when it is configured properly. It provides protection and notifications for traffic on both Public and Private networks. For portable devices, the Public settings should be carefully reviewed. You can allow or block incoming/outgoing traffic entirely or allow certain apps or features through. The advanced settings provide precise control over the firewall activity, allowing you to control each inbound and outbound rule. You’ll probably be surprised at the number of rules. Shown below is the Windows Defender Firewall with Advanced Security window. A portion of the inbound rules is being displayed.

Windows Defender Firewall with Advanced Security
SecureDNS
Secure DNS is useful in combating Phishing attacks. This service is most effective when the IP configuration uses settings specifically recommended by the ISP. That does it for 2.4! See you in 2.5! Good luck on the test!

By continuing to browse this site, you accept the use of cookies and similar technologies that will allow the use of your data by CertBlaster in order to produce audience statistics- see our privacy policy.